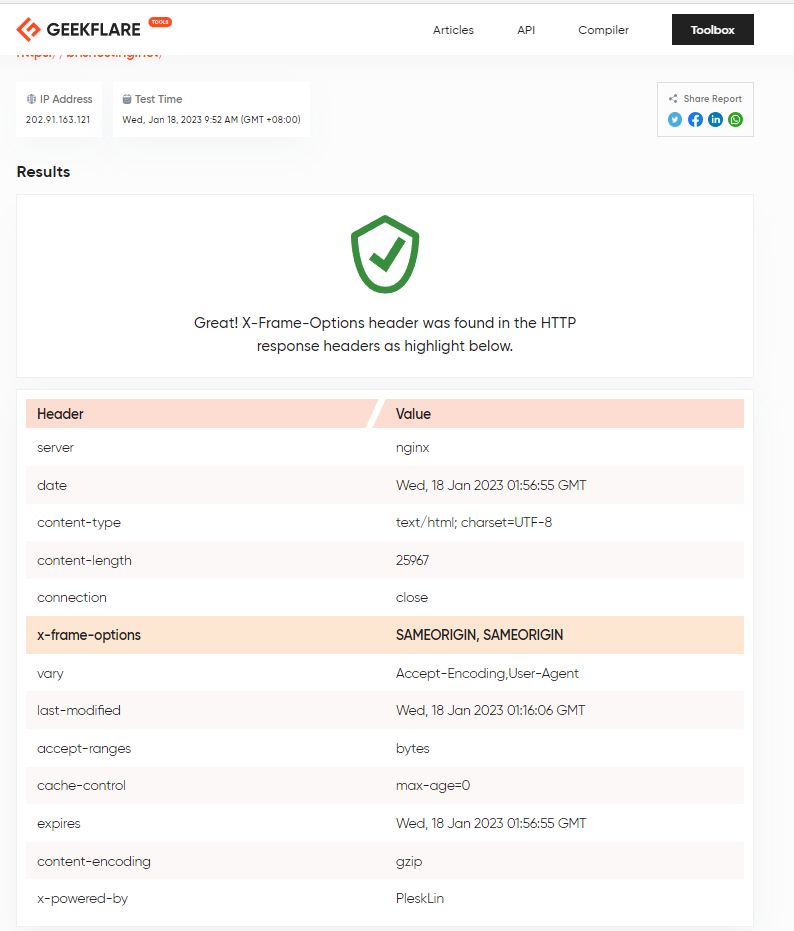
You can use this to test out your webserver:
https://geekflare.com/tools/x-frame-options-test
Category: Philippine Web Developers
How to Optimize Your Moodle Server
 To increase the performance of your Moodle site, there are a number of ways to optimize your server. You should avoid enabling multiple filters, because this can increase the server’s load. Instead, consolidate features into smaller plugins and turn off filters that are rarely used. A great example is the Multi-Embed filter. It allows you to embed content from third-party websites and services and converts the URL into an embedded format.
To increase the performance of your Moodle site, there are a number of ways to optimize your server. You should avoid enabling multiple filters, because this can increase the server’s load. Instead, consolidate features into smaller plugins and turn off filters that are rarely used. A great example is the Multi-Embed filter. It allows you to embed content from third-party websites and services and converts the URL into an embedded format.
To optimize your server, first, create a baseline benchmark. You can measure the performance of your system by looking at how long it takes to load a page. If the page is taking too long to load, try to decrease the number of sections that appear on a page. The smaller the pages are, the less RAM they take up, so this will increase your server’s performance. If you’re worried about RAM usage, you can use folders and core activities.
You should also make sure that your server can handle the load. Moodle requires a good amount of RAM and disk space. In addition, your host and browser must be high-performing. You should monitor the performance of each of these components monthly. If you don’t manage to achieve this, you might need to purchase a new computer. If you’re using Moodle on a server, the best way to optimize it is to purchase a powerful computer and upgrade it if necessary.
Learn Tips & Tricks on Basic Principles of Design
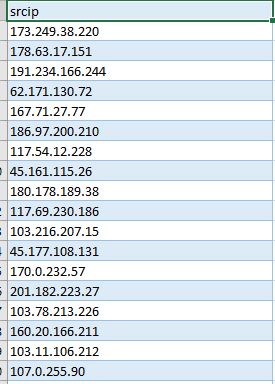
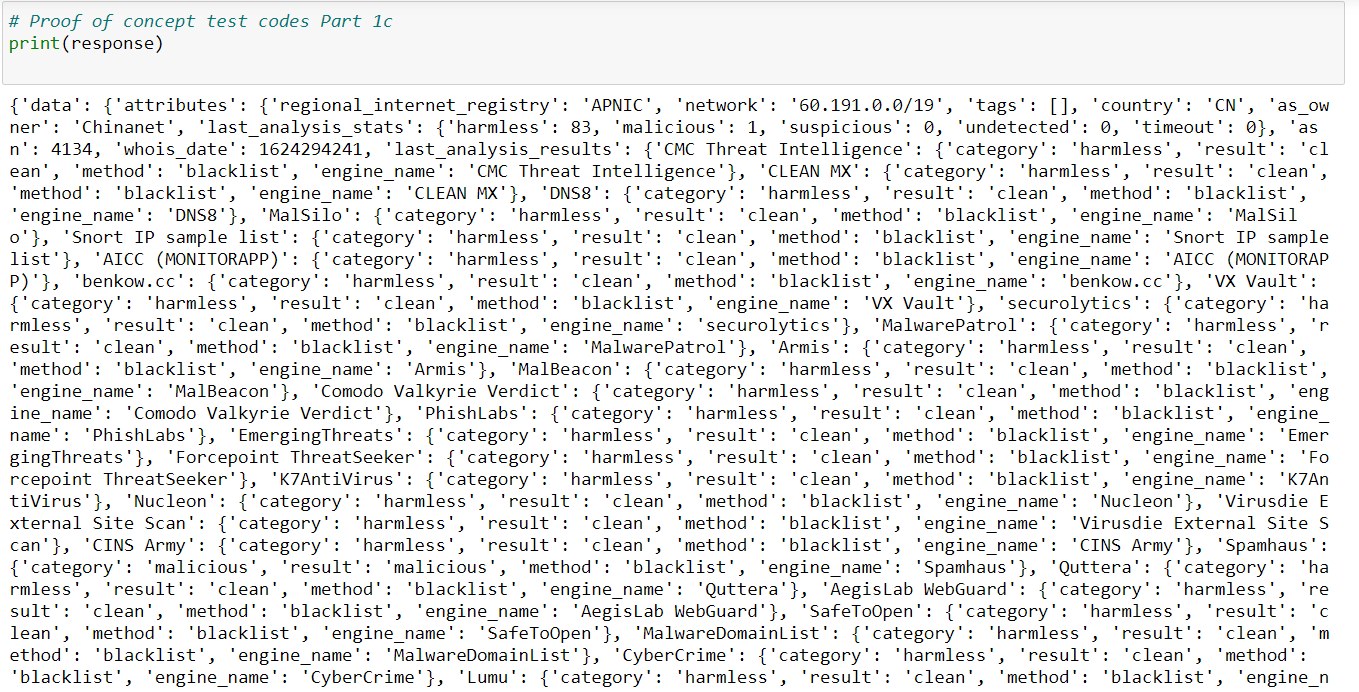
When you need to send abuse emails to thousands of botnet IP addresses, automate it with Python and virustotal.com’s API.
BNS Featured by websiteplanet.com
BNSHosting is delighted to be featured by international webhosting review site, websiteplanet.com. Check out the interview: https://www.websiteplanet.com/blog/bnshosting-interview/
BNS Featured by WebsiteHosting.co.uk
BNSHosting is delighted to be featured by international webhosting review site, Websitehosting.co.uk. Check out the interview: https://www.top10-websitehosting.co.uk/bns-hosting-review-and-interview/