Category: Technical Resources
PSU Alaminos Interns help deploy Starlink
Dagupan City, Philippines – PSU Alaminos interns helped deploy Starlink internet in the UPICT event dubbed: “Dagupan Stakeholders Meeting”, with the supervision from bnshosting senior staff Bryan Arafilles. It also saw the use of Dual WAN WiFi Router. This deployment marks a significant milestone in the effort to bring fast, reliable, and affordable internet access to communities in the Philippines.
The PSU Alaminos interns provided invaluable manpower during the deployment process, helping to do site survey, set up the necessary infrastructure and providing technical assistance to ensure that the deployment was successful. Their contributions were essential in making this deployment a success.
Bnshosting.net played a critical role in the deployment, providing the necessary equipment and technical expertise to ensure that the deployment was successful. The company’s commitment to providing reliable and affordable internet solutions has been instrumental in the effort to connect communities in the Philippines.
The deployment utilized a Dual WAN WiFi Router, which allowed for the use of two different internet connections simultaneously, providing increased reliability and faster speeds. This innovative solution has been instrumental in overcoming the challenges of deploying internet solutions in remote areas.
The successful deployment of Starlink in Dagupan Stakeholders Meeting is a testament to the power of collaboration and the importance of providing reliable and affordable internet access to communities. It is our hope that this deployment will serve as a model for future efforts to connect communities throughout the Philippines.
Picture shows the various preparation steps done by the PSU Alaminos Interns to help deploy Starlink internet at the CSI Stadia for the UPICT Dagupan Stakeholders’ meeting.
BNSHosting.net Adds Starlink connection
BNSHosting.net expanded our redundancy by ordering Starlink. This provides our Customers with More Reliable and High-Speed Internet Access.
In recent years, SpaceX’s Starlink satellite internet service has been making waves in the world of telecommunications. With its low latency, high-speed, and global coverage capabilities, Starlink is poised to revolutionize the way we connect to the internet. And for businesses with data centers, adding a Starlink satellite to their existing infrastructure can have numerous benefits for their customers.
First and foremost, adding a Starlink satellite to an existing data center can greatly improve the reliability and availability of the internet connection for customers. With its global coverage and redundancy, Starlink can ensure that internet access remains uninterrupted even in the event of a local outage or disruption. This is especially critical for businesses that rely heavily on the internet to conduct their operations, such as e-commerce sites or financial institutions. By providing a more reliable connection, businesses can minimize the risk of downtime and ensure that their customers can always access their services.
Another key benefit of adding a Starlink satellite to a data center is the increased speed and bandwidth it can provide. Starlink’s high-speed internet can provide customers with faster access to data and applications, which can improve their productivity and efficiency. In addition, the increased bandwidth can enable businesses to expand their online offerings and provide customers with more comprehensive and feature-rich services.
Perhaps one of the most significant benefits of Starlink is its low latency. Unlike traditional satellite internet services, which often suffer from high latency due to the time it takes for signals to travel to and from orbit, Starlink’s low-earth orbit satellites can provide latency as low as 20ms. This is a game-changer for businesses that require real-time data access or low-latency communication, such as online gaming or video conferencing. With Starlink, businesses can provide their customers with a seamless and responsive experience that rivals traditional wired connections.
Finally, adding a Starlink satellite to an existing data center can provide businesses with a competitive advantage. By offering faster, more reliable, and more feature-rich internet services, businesses can differentiate themselves from their competitors and attract more customers. In addition, the global coverage provided by Starlink can enable businesses to expand their reach and offer their services to customers in remote or underserved areas.
From increased reliability and availability to faster speeds and low latency, Starlink’s unique capabilities can help businesses improve their online offerings and differentiate themselves in a competitive market. As Starlink continues to expand its coverage and capabilities, we can expect to see more and more businesses take advantage of this innovative technology.
How to Stop SMS scams on your PHONE
The SMS scams are in the news lately. Here is what you need to know. In Australia, SMS scams have caused as much as 381m in losses.
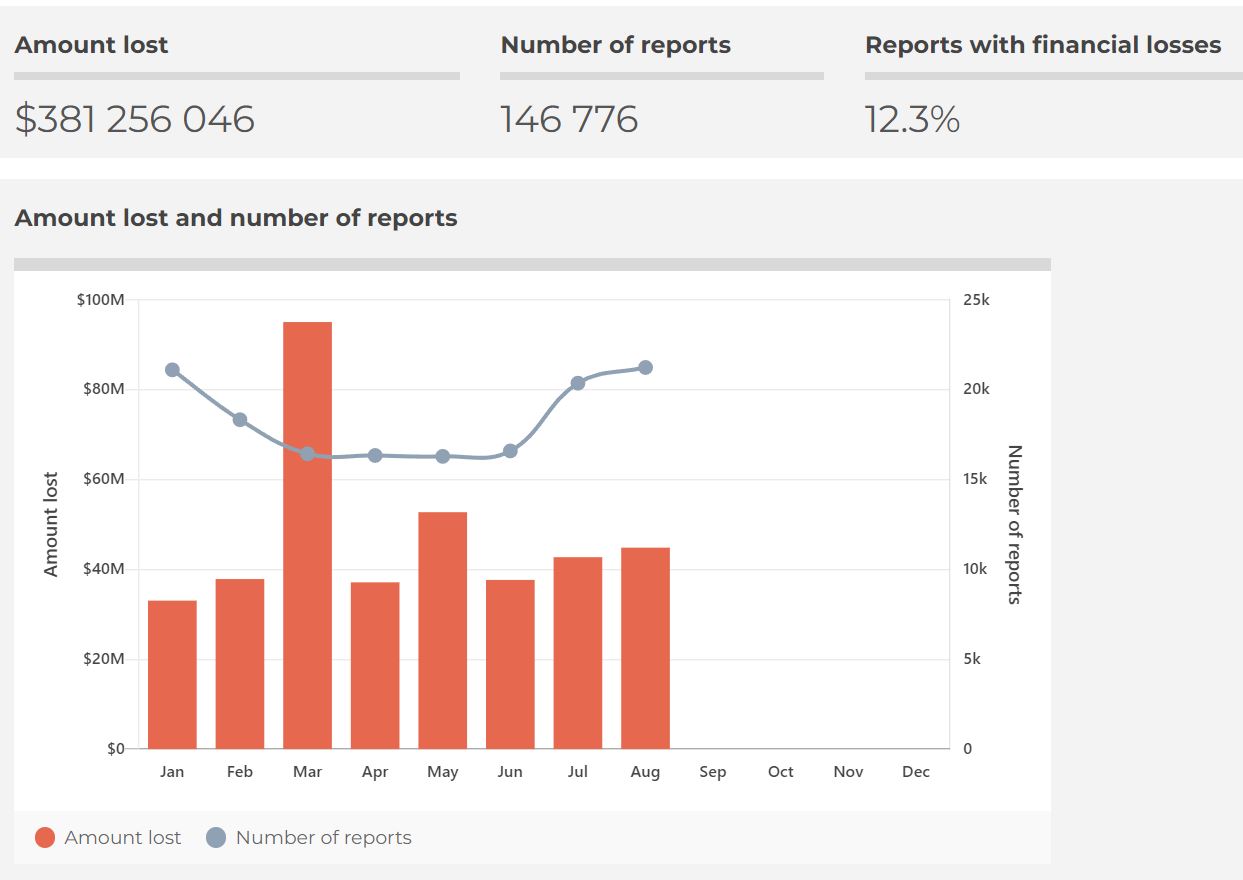
While the Telcos and Government grapple with what best to do to reduce this, there are something you can do to stop spam on your mobile phone. You can block these spams by tagging them!
For iPhone, all you need is in Settings
Got a spammy-looking message in your Messages inbox? As long as you have iOS 7 or later installed on your iPhone, the steps are pretty simple. Open the message, tap Contact, then tap the little “i” button that appears.
Next, you’ll see a (mostly blank) contact card for the spammer who sent you the message. Scroll down to the bottom of the screen and tap “Block this caller.” C-ya, spammer.
For Android, it’s a little more complicated
The SMS-blocking situation for Android is a bit more complex than for iOS—although to be fair, it wasn’t possible to block text messages on the iPhone at all until iOS 7 came around.
While the “stock” Messaging app won’t let you block SMS spammers, there’s a plethora of apps on the Google Play store that’ll do the job…or used to, anyway.
Working in tandem with the standard Messaging app, third-party SMS-blocking apps (like SMS Filter or Mr. Number) let you create and manage what’s called a “blacklist”—that is, a list of phone numbers that you don’t want to hear from again. Other anti-spam apps, like Postman and Spam Blocker, will go ahead and flag suspected SMS spam.
But thanks to a new restriction in the latest version of Android—namely, that only one app at a time may tap into your SMS messages—many of these handy SMS spam-blocking apps have been rendered useless.
Now, it’s very possible that your particular Android phone hasn’t been updated to Android “KitKat” yet, in which case you’re free to shop around for a dedicated SMS blocking app.
Source: https://www.pcworld.com/article/436450/how-to-stop-sms-spam-on-your-android-or-ios-phone.html
How to Optimize Your Moodle Server
 To increase the performance of your Moodle site, there are a number of ways to optimize your server. You should avoid enabling multiple filters, because this can increase the server’s load. Instead, consolidate features into smaller plugins and turn off filters that are rarely used. A great example is the Multi-Embed filter. It allows you to embed content from third-party websites and services and converts the URL into an embedded format.
To increase the performance of your Moodle site, there are a number of ways to optimize your server. You should avoid enabling multiple filters, because this can increase the server’s load. Instead, consolidate features into smaller plugins and turn off filters that are rarely used. A great example is the Multi-Embed filter. It allows you to embed content from third-party websites and services and converts the URL into an embedded format.
To optimize your server, first, create a baseline benchmark. You can measure the performance of your system by looking at how long it takes to load a page. If the page is taking too long to load, try to decrease the number of sections that appear on a page. The smaller the pages are, the less RAM they take up, so this will increase your server’s performance. If you’re worried about RAM usage, you can use folders and core activities.
You should also make sure that your server can handle the load. Moodle requires a good amount of RAM and disk space. In addition, your host and browser must be high-performing. You should monitor the performance of each of these components monthly. If you don’t manage to achieve this, you might need to purchase a new computer. If you’re using Moodle on a server, the best way to optimize it is to purchase a powerful computer and upgrade it if necessary.
How to Optimize Maria SQL for Websites

The first step in optimizing your MySQL server is to make sure it is using a secure connection, preferably HTTPS. This is important for your site’s security as well as for your website’s performance. You can optimize your server to run as fast as possible by ensuring it uses a secure connection. Once you have the right database server, you can begin working on your website. Here are some tips to optimize Maria SQL for your site.
First, make sure you’re using appropriate monitoring tools for your MariaDB database. There are many free tools available, including ClusterControl. This tool offers performance advisors, alarms, and alerts for MariaDB. Besides, it’s open source. If you’re planning to use the database for a large website, you should consider increasing the threadpool variable to a higher value. Once you’ve done that, you should increase your backlog to a minimum of 100MB and then add a new one for each table partition.
To make your MariaDB database run faster, you should allocate at least one KB of memory for each table. For best performance, allocate 1 KB per MB of memory. Alternatively, use mrr_buffer_size to make your tables larger. By adjusting the maximum heap size, you’ll be able to get a better performance. After all, you should always have a spare tire for your databases.