Have you tried out CloudFlare’s Turnstile API as an alternative to CAPTCHAs? Do share with our community and leave your comment below.

Have you tried out CloudFlare’s Turnstile API as an alternative to CAPTCHAs? Do share with our community and leave your comment below.

Source: https://www.theguardian.com/business/2022/sep/29/optus-data-breach-everything-we-know-so-far-about-what-happened
Optus says the stolen data includes names, email addresses, postal addresses, phone numbers, dates of birth, and for a portion of the affected customers, identification numbers including passport numbers, driver’s licence numbers and Medicare numbers.
The dump of records released by the forum user contained all this information.
“Unfortunately, it can be pretty common,” Josh Lemon, a digital forensics and cyber incident expert at SANS Institute, said. But he said attackers tended to not target a single organisation. They usually scan across the internet looking for known vulnerabilities and exploiting those vulnerabilities all at once, he said.
“So for a threat actor to specifically just go after [one company] is a little bit unique in that sense.”
In an email sent to its members on Friday, Sep. 16, the coffee chain said that it had discovered “unauthorised activity online” and “some unauthorised access” to customer details, such as name, gender, date of birth, mobile number, email address and residential address.
Following this incident, Starbucks added that relevant authorities have been informed and that the firm is assisting them on this matter.
Short story:
Home-grown fashion label Love, Bonito has been fined $24,000 over a 2019 data breach which saw personal information of more than 5,500 customers compromised. The root cause: The administrator account of a software used by Love, Bonito was compromised. It was used to manage its e-commerce website. An unknown third party accessed and obtained customers’ personal data via this gap.
Countermeasure: Try to apply Access control list to sensitive parts of your webapp. So that even if the admin account was compromised, it could not log in from just anywhere. It had to be accessed from within specific locations. Also enable multi factor authentication.

Source: https://www.straitstimes.com/tech/tech-news/love-bonito-fined-24000-over-data-breach-involving-over-5500-customers
The short story:
HOSPITALITY platform RedDoorz was found to have leaked the details of 5.9 million customer records in the largest data breach incident since Singapore’s Personal Data Protection Act came into force. The root cause was traced to the API key embedded in the mobile app that the developers used.
Even if ReDoorz had several pentests done. The mobile app was not screened. It however helped to reduce the overall fines levied on it.

Source: https://www.businesstimes.com.sg/garage/data-breach-at-reddoorz-hit-6m-customers-hospitality-platform-fined-s74000
Source: Cisco Breached by Ransomware Gang, 2.75GB Reportedly Stolen (webpronews.com)
Cisco confirmed the Yanluowang gang compromised the company’s network but said the bad actors only made off with non-sensitive data. The data was from an employee’s Box folder.

“Microsoft released its monthly security update Tuesday, disclosing more than 120 vulnerabilities across its line of products and software, the most in a single Patch Tuesday in four months. This batch of updates also includes a fix for a new vulnerability in the Microsoft Windows Support Diagnostic Tool (MSDT) that’s actively being exploited in the wild, according to Microsoft. MSDT was already the target of the so-called “Follina” zero-day vulnerability in June. Two of the important vulnerabilities CVE-2022-35743 and CVE-2022-34713, are remote code execution vulnerabilities in MSDT. However, only CVE-2022-34713 has been exploited in the wild and Microsoft considers “more likely” to be exploited.” – SANS @RISK
In its 2022 Global Threat Report, CrowdStrike warned that cyberattacks are “moving beyond malware” and increasingly “living off the land,” or using legitimate credentials and built-in tools to access their victims’ networks. Of all the detections indexed by CrowdStrike Security Cloud in the fourth quarter of 2021, the report said, 62% of them were malware-free, “exploiting stolen user credentials and identity to bypass legacy security solutions.”
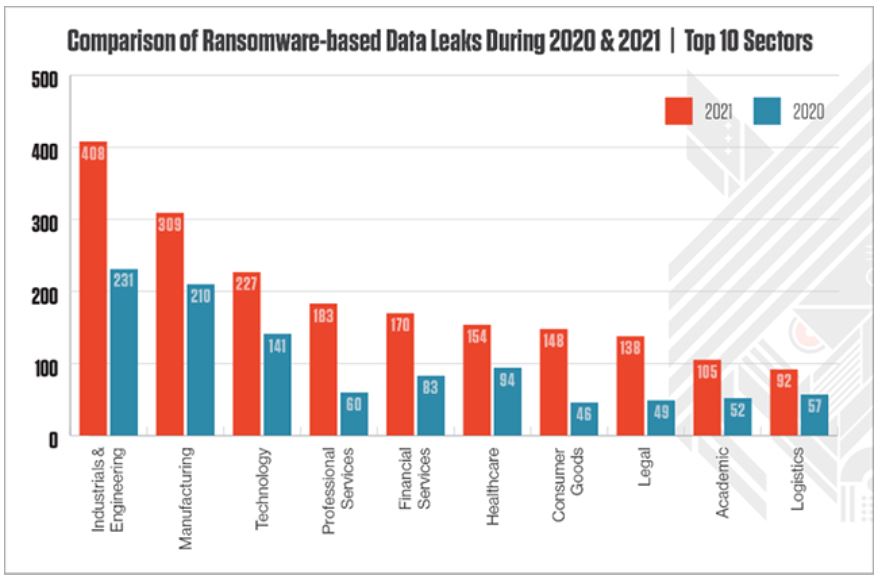
Source: https://thejournal.com/articles/2022/02/15/cybercrime-report-shows-2021-ransomware-data-leaks-doubled-in-education-sector.aspx