Category: Technical Resources
Scary Data – Trends in Malware, Phishing, Site Cleaning and Bad Networks
Almost Half a Million Malware Sites
The number of Malware sites continues to grow, hitting a new peak of 489,801 in October of 2015. That is up over 160% from the same time the previous year. As we have discussed before, a website that is infected with malware can install malicious software on your computer if you visit it. Attackers use the software to steal sensitive information from you such as credit card information and social security numbers.
As an internet user, the growth in malware sites means that the odds of you accidentally visiting one and becoming infected continue to increase. Google and the other search engines do a decent job of flagging them, but they can’t catch all of them in time to provide complete protection.
As a website owner, it means that attackers are having more success than ever compromising websites. It goes without saying that we think you should take website security seriously.
150% Growth in Phishing Sites in 7 Months
According to Google there are now 293,747 phishing sites on the internet, up from 113,132 in July of last year. This represents growth of over 150% in a mere seven months. A phishing site attempts to trick you into thinking it is legitimate, like your online bank or an online retailer. They then lure you into providing login credentials or other sensitive information. In the Introduction to WordPress Security article in our Learning Center we talk about how attackers are even using phishing tactics to steal WordPress credentials.
It’s taking webmasters up to 90 days to respond
Google measures how long it takes for webmasters to take action after they have received notice that their site has been compromised. Over the last year, the fastest average webmaster response time reported was 61 days, and for much of the year it was 90 or worse.
Which neighborhoods to avoid on the internet
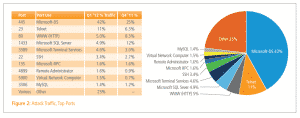
Google provides very interesting data about the rate of infection for differentAutonomous Systems on the internet. An Autonomous System is a network level designation that represents a pool of IP addresses that are under the control of one or more networks on behalf of a single entity. You can think of it roughly as the group of IP addresses that have been assigned to an ISP. The data is very interesting, and aligns with what we learned in the analysis of brute force attacks we did a few weeks ago.
The thing that jumps out the most to us is the incredibly high penetration of infection on some Autonomous Systems. With infection rates as high 49%, there are areas of the internet that we would strongly encourage you to avoid. If you want to check out what Autonomous System your IP address belongs to, simply enter it into this handy tool. The good news is that the large majority of Autonomous Systems have infection rates of 1% or lower. We hope that Google’s reporting will serve as a call to action for the networks with the biggest problems.
More information about this: https://www.wordfence.com/blog/2016/02/trends-malware-phishing/?utm_source=list&utm_medium=email&utm_campaign=trendsmal1
Free Ecommerce/Web Dev Security Training

This training program is conducted in partnership with Isaac Sabas and Jonathan Mantua of Pandora Security Labs. (offers advance IT security training and provider of WebRanger – an online security monitoring and attack blocking service)
Training objectives:
- Learn about web application security threats and how to mitigate them.
- Learn and apply secure programming best practices.
- Learn and perform web application testing.
Target audience:
- Entrepreneurs who would like to under how e-commerce security works and become tech-savvy when dealing with web developers and Internet security specialists.
- E-Commerce developers who would like to level-up their capabilities by building and maintaining secure websites.
More Details: http://ecommercebootcamp.digitalfilipino.com/course/e-commerce-security-course/
PHNOG Conference 2016
The Department of Science and Technology – Advanced Science and Technology Institute (DOST-ASTI), in partnership with the Philippine Network Operators’ Group (PhNOG), and Trans-Eurasia Information Network (TEIN) Network Cooperation Center (TEIN*CC) will be conducting a one (1)-day Conference with the theme ‘”All over IP’ (AoIP) – touching the different facets of Internet, entwined to our daily lives” on 25 January 2016 at the Marriott Grand Ballroom, Marriott Hotel Manila, Pasay City, Metro Manila.
| 1100 | Big Data Analytics Applied in Network Operations | Wilson Chua/Bitstop |
| 1130 | IXP Next steps (advantages and disadvantages) | Daishi Shima/BBIX |
| 1200 | Lunch break | |
| 130 | Management and Sustainability of the IXP – taking it to the next level – Global Examples / DNSSEC | Jane Coffin/ISOC, Kevin Meynell/ISOC |
| 200 | Internet enabled businesses (challenges/milestones) | Rhett Jones/Rise |
| 230 | CDNs and Internet traffic Analystics | Kam-Sze Yeung/Akamai |
| 300 | Role of a Peering Manager | Jake Chin/Google |
| 330 | Break time | |
| 400 | Network Security | Mon Nunez |
| 430 | Internet BCPs | Amante Alvaran/Brocade |
| 500 | Evolution of the Network Engineer Job Role | Ceejay Dideles |
| 530 | IOT | Benjie Tan |
| 600 | Closing |
Said activity aims to gather participants from the R&D and IT/ICT communities together with the current PhNOG members to discuss the opportunities that can be derived from joining and using the TEIN Network. TEIN is a high speed international research network which provides access to researchers and research institutions within participating countries in Asia and Europe. Through TEIN, international joint research projects pertaining to climate change, remote medical service, remote cultural performances, agriculture, and information technology have been conducted. Local and foreign experts will also share their knowledge and experiences that will enable the continuous development of the Philippine Internet.
On the other hand, Philippines Network Operators Group (PHNOG) is a nonprofit organization established to promote coordination among Network Operators in Philippines. Focus is given to knowledge development of all members as well as the Philippines IT community as a whole through discussions on technical issues/concerns regarding the Internet and network management.
In line with this, we would like to invite you as one of the participants in this one (1)-day activity. Registration for this activity is free. Please take note that the activity only offers limited slots, which will be granted on a first come, first served basis. Deadline for registration is on 15 January 2016. To reserve your seat, kindly register at this link: https://www.apan41manila.com/events/register/xphilippine-network-operators-group-conferenc
Should you have any clarifications, please feel free to contact Mitz Ann N. Montañez at mitz@asti.dost.gov.ph or Marie Antoinette F. Bangabang at meiann@asti.dost.gov.ph. You may also call +63 2 4269760 loc. 1603 / loc.1408.
Joomla GoogleMap Proxy Vulnerability
If you are using Joomla and have the Googlemaps plugin, your webserver may be under attack and being used to attack others via cross site scripting.
The problem with the Joomla! Googlemaps plugin lies in the fact anyone can request the
/plugins/system/plugin_googlemap2_proxy.phpin their browser or script, to execute cURL HTTP requests to remote websites. Theurlparameter is vulnerable for Cross Site Scripting (XSS) attacks, and allows the retrieval of remote website content. When this happens a lot, a website becomes overloaded and unresponsive, making a Denial-of-Service attack succesfully executed. This is not only a problem for the website owner on the remote end, or its hosting company. Your web servers transmit a lot of HTTP traffic to remote ends, increasing server load, usage and network bandwidth (for which you pay). Therefor it’s important to stop this abuse.
To remedy this, you can remove the plugin or restrict access to the file via your .htaccess.
More info here: https://www.saotn.org/joomla-websites-abused-open-proxy-denial-service-attacks/
Google Map proxy
BNS Founder interviewed by Telecoms Asia
“To Peer or Not to Peer”
Last month, the Philippine Senate conducted a hearing to investigate the reason behind the country’s slow and expensive internet connection. What prompted the probe was an infographic posted by ASEAN DNA on Facebook showing the Philippines in the bottom three Southeast Asian countries with the slowest average internet speed, based on an Ookla speed test. That post has since gone viral, especially among disgruntled Filipino netizens.
Local IP peering was one of the possible solutions mentioned at the hearing by no less than the regulator, the National Telecommunications Commission (NTC). Soon after, a number of articles on IP peering began making the rounds on social media. There was even a change.org petition urging PLDT, the incumbent telco and largest ISP, to do local IP peering.
Now what does this tell us? The demand for better internet service has reached such a critical point that even the ordinary customer is becoming interested in something as technical as IP peering.
How and why is peering important to getting faster and more affordable internet connection?
To help answer this, I had a chat with Wilson Chua, managing director and co-founder at Bitstop Network Services, Inc. Starting out in computer distribution, Bitstop next ventured into operating a franchise of paging service EasyCall and promoting Mozcom in the province of Pangasinan before branching out to call centers and data-center operations via BNShosting.net. Bitstop was the first local ISP to peer via the Philippine Open Internet Exchange (PHOpenIX), the only publicly funded, neutral, and non-profit internet exchange point in the country. Below, Chua responds to my questions on peering and how it is benefiting Philippine internet.
TA: Can you explain what local IP peering is and how it benefits an ISP like Bitstop?
Local peering happens when two or more network operators decide to “meet” each other at a common point (the internet exchange or IX). When peering, an operator agrees to let others use the interconnection link to pass traffic from its own network to another operator’s network, and vice versa. By doing so, both parties benefit from a reduction of bandwidth by using the cheaper direct links instead of the costly international circuits. Operators who peer also agree to not charge the other party for the traffic, so neither party pays for the exchanged traffic.
Local peering has several benefits:
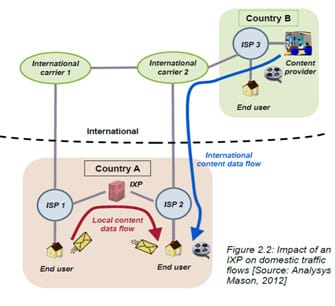
- Faster access times. Our hosted clients benefit from having their sites connected directly to the local internet community in the Philippines via the shortest distance possible. This improved network performance is one of the main reasons for connecting to the IXP. In an illustration (below) from a reportby Analysys Mason and Internet Society, you can see that users of ISP1 can get to ISP2 via direct peering links (red line with arrow). Without this peering, ISP1 users will have to go out of the country, use the expensive international links, pass via another carrier, and then on to another ISP3, before getting back to the country to reach ISP2. The same process happens vice versa. This is inefficient and slow, and can burden international bandwidth resources.
- Resiliency. As the Philippines is located in the Ring of Fire and the Typhoon belt, we see that most carriers’ links are affected by earthquakes and storms from time to time. When some of these links go down, the IX can provide an alternative path for the traffic of various operators to pass to get to each other’s local network. Going back to the illustration, suppose ISP1’s link to International Carrier 1 (purple line) goes down (like in the case of the Taiwan earthquake). Without the peered links (red line), ISP1 users will not be able to talk to ISP2 users.
- Community relationships. Since the exchange puts system admins in regular contact with each other, we find it easier to form communities of interest and help each other out with common issues like security (e.g., hacking and cyber-attacks).
- Efficient marketplace for bandwidth. Some of the IXPs have evolved into a universal market place to buy bandwidth from other peered partners. Peered partners can buy from other peers with excess bandwidth capacity, for the former to fill up spikes in their traffic. This effectively provides a market-based mechanism for internet pricing—one that is not subject to “lockdowns” by current providers.
TA: When did you start peering? How did you find out about the PHOpenIX?
I was influenced by APNIC and Dr. William Norton, both of whom have been highlighting the power and benefits of peering exchanges since the 1990s. So from the early days, we were peered with PLDT’s PHIX. However, they price their local loop (last mile) so high such that all the other peered partners could only put in small links. This wasn’t enough to sustain the local community. Imagine a peering point with 2mbps links only. Later on, the Manila Internet eXchange (MIX) and BayanTel’s NIGX offered us a connection. We connected to these as well, but since they were telcos, I couldn’t see other telcos and ISPs connecting to these exchanges.
When I heard that the government was developing a neutral peering point, the PHOpenIX, I immediately signed up from day one. Since then, we have grown our link from a measly 512kbps to 50mbps today.
TA: What considerations did you take before deciding to peer via the PHOpenIX?
It had to be sustainable and had to have the potential of getting a critical mass of operators using it. Peering has what we call Network Efforts. As more networks are connected, the value of the peering point increases. As the Metcalf Law states, “The value of the telecommunications network is proportional to the square of the number of connected users of the system.” I think the PHOpenIX is about to reach that critical mass of users with news of more operators coming in and peering.
Source: http://www.telecomasia.net/blog/content/peer-or-not-peer-conversation-bitstopph
Why You Should Learn to Run a Server Before You Learn to Code
To the disappointment of everyone who wants to learn to code so they can get rich or powerful, developer Dave Winer tells us that’s probably not going to happen. He lists good reasons why you might want to learn to code, but recommends you learn to run a server first.
Learning to code is good if you have a calling, if you feel it’s what you must do to express yourself. If you have ideas that you can implement in code that no one else is doing. Or if you just love the puzzles that programming is constantly presenting you with. You have to have a certain amount of self-hatred to love programming, btw, because it’s a grind. And to do it well you have to have a lot of all of these things.
You might think that by learning to code you get to be the Man Behind the Curtain, the all-powerful person who makes the digital world work. But that’s not what coding is about. If you want power, and I’ve said this many times — rather than learn to code — first learn to run a server. That’s real power. And it’s far easier than programming.
Plus, running a server, Winer says is a gateway into programming.
source link for this nice article: http://lifehacker.com/why-you-should-learn-to-run-a-server-before-you-learn-t-1497178889?utm_campaign=socialflow_lifehacker_facebook&utm_source=lifehacker_facebook&utm_medium=socialflow
Mobile Data Protection
Xyon Systems and Services, Inc. would like to introduce you to Evault Endpoint Protection, an all-in-one laptop backup, recovery, and data security solution to control data across your mobile workforce. To get started, simply complete the form below to download any of the resources or to schedule a free consultation.
http://xyon.com.ph/evault.php
BNSHosting Needs YOU
If you are looking for a challenging and rewarding career in data center operations in Dagupan City, Philippines, look no further! We are in need of *nix system administrators and LAMP interns (Linux, Apache, Mysql, PHP) that are willing to learn and be trained.
We have a great track record of training and developing our team members into extremely proficient data center engineers. Most of our ex staffers are now in teaching professions or in Data centers here and abroad.
Here is your chance to join a great team! Apply now. Email us at team[at]bnshosting.net