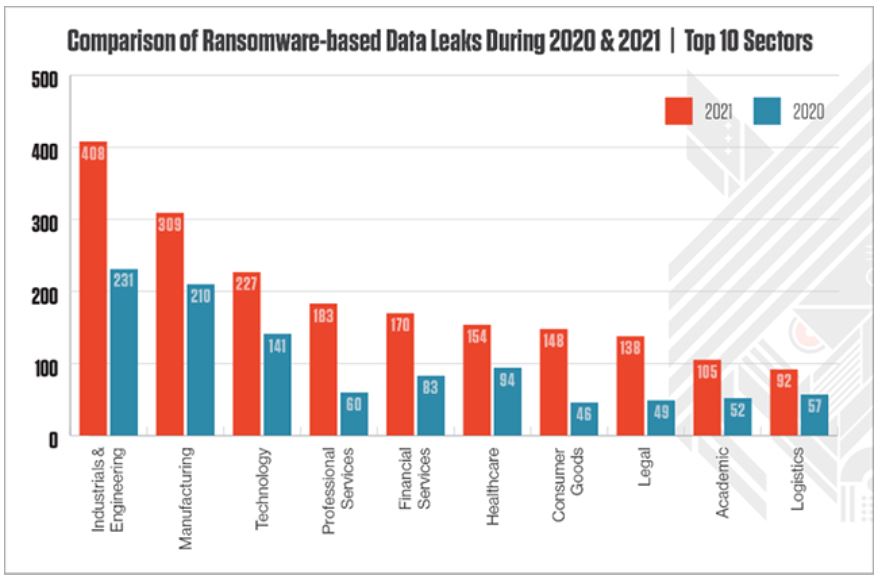
The SMS scams are in the news lately. Here is what you need to know. In Australia, SMS scams have caused as much as 381m in losses.
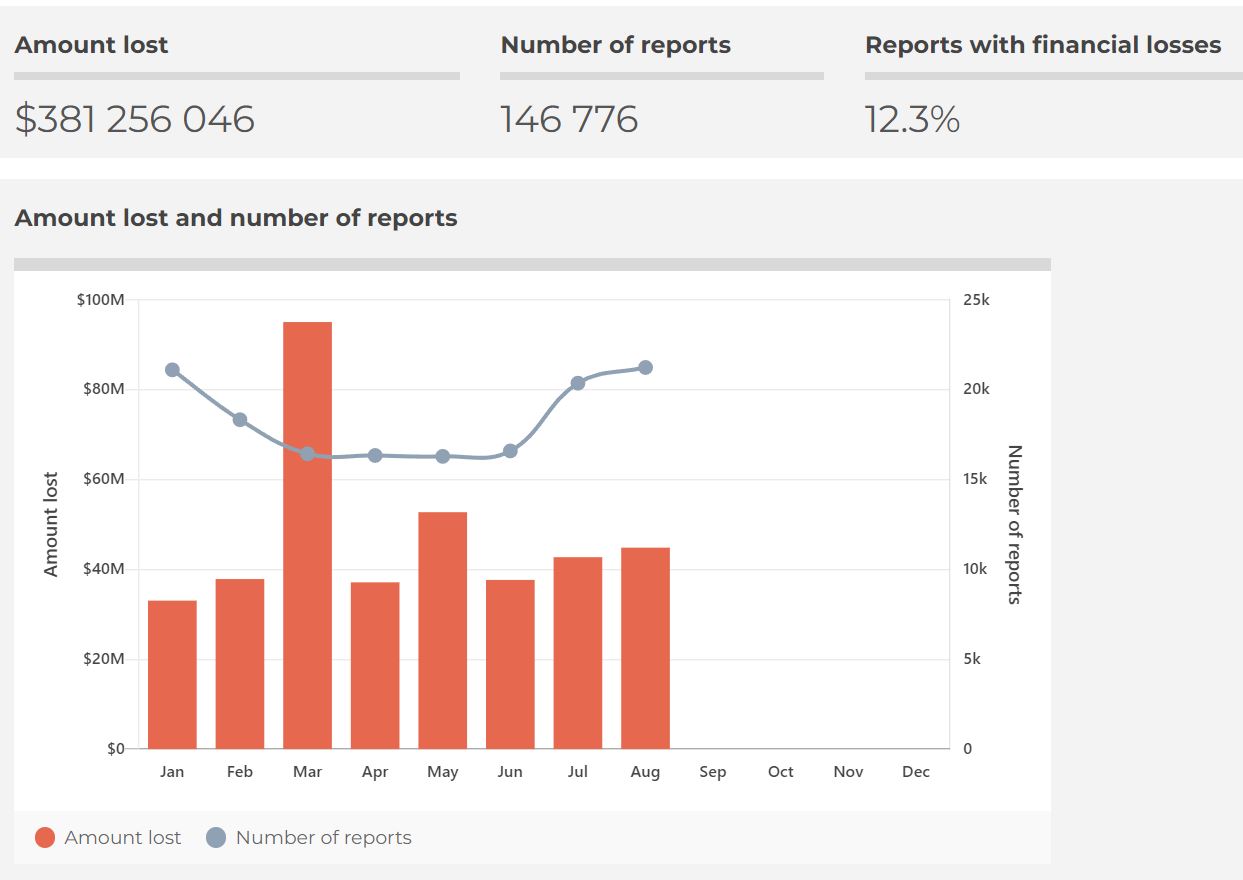
While the Telcos and Government grapple with what best to do to reduce this, there are something you can do to stop spam on your mobile phone. You can block these spams by tagging them!
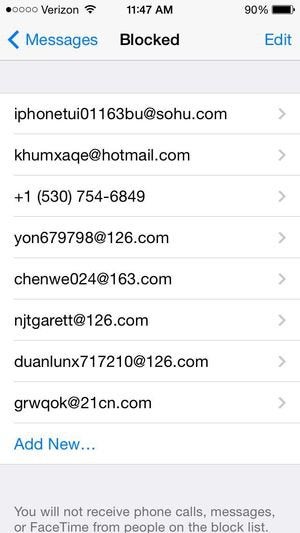
For iPhone, all you need is in Settings
Got a spammy-looking message in your Messages inbox? As long as you have iOS 7 or later installed on your iPhone, the steps are pretty simple. Open the message, tap Contact, then tap the little “i” button that appears.
Next, you’ll see a (mostly blank) contact card for the spammer who sent you the message. Scroll down to the bottom of the screen and tap “Block this caller.” C-ya, spammer.
For Android, it’s a little more complicated
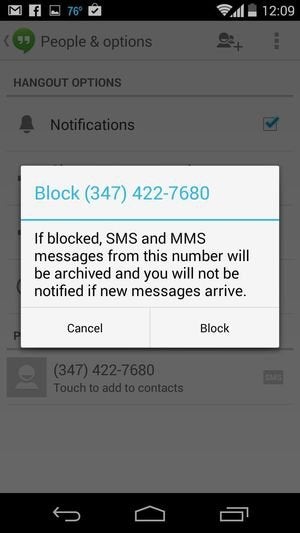
The SMS-blocking situation for Android is a bit more complex than for iOS—although to be fair, it wasn’t possible to block text messages on the iPhone at all until iOS 7 came around.
While the “stock” Messaging app won’t let you block SMS spammers, there’s a plethora of apps on the Google Play store that’ll do the job…or used to, anyway.
Working in tandem with the standard Messaging app, third-party SMS-blocking apps (like SMS Filter or Mr. Number) let you create and manage what’s called a “blacklist”—that is, a list of phone numbers that you don’t want to hear from again. Other anti-spam apps, like Postman and Spam Blocker, will go ahead and flag suspected SMS spam.
But thanks to a new restriction in the latest version of Android—namely, that only one app at a time may tap into your SMS messages—many of these handy SMS spam-blocking apps have been rendered useless.
Now, it’s very possible that your particular Android phone hasn’t been updated to Android “KitKat” yet, in which case you’re free to shop around for a dedicated SMS blocking app.
Source: https://www.pcworld.com/article/436450/how-to-stop-sms-spam-on-your-android-or-ios-phone.html