Certificates of attendance and appreciation for wordpress optimization workshop conducted on January 25, 2020 @Bitstop Network Services, inc.
Category: Events
Have you heard of Foreman?
What is Foreman?
Foreman is an open source project that helps system administrators manage servers throughout their lifecycle, from provisioning and configuration to orchestration and monitoring. Provisioning support gives you easy control of setting up new servers, and using configuration management (Puppet, Ansible, Chef and Salt are supported), you can easily automate repetitive tasks. With Foreman, you can quickly deploy applications, and proactively manage change, both on-premise with VMs and bare-metal or in the cloud. Foreman scales well to multiple locations (offices, data centres, etc) and multiple organisations, allowing you to grow without losing your single source of infrastructure truth.
WordPress Site Optimization by Tzar Umang

Learn how Tzar Umang dealt with a WordPress site, whose size was around 5GB to eventually load in 2 seconds!
Tzar will share with the participants the tools that he used:
1. WP Rocket
2. Auto-optimize
3. Imagify.io (ultra compression)
Server Side:
1. PHP Compress – cPanel
2. Content Delivery // Packet Compression (made with python)
To reserve your slot, kindly register for the FREE event here.
Increased Vigilance Urged in Spillover of US-IRAN conflict on cyber arena
Here are some primer and tips from the US Homeland Security on securing your network against potential collateral attacks and damage brought on by the US-Iran conflict.
Alert (AA20-006A)
Potential for Iranian Cyber Response to U.S. Military Strike in Baghdad
Recommended Actions
The following is a composite of actionable technical recommendations for IT professionals and providers to reduce their overall vulnerability. These recommendations are not exhaustive; rather they focus on the actions that will likely have the highest return on investment. In general, CISA recommends two courses of action in the face of potential threat from Iranian actors: 1) vulnerability mitigation and 2) incident preparation.
- Disable all unnecessary ports and protocols. Review network security device logs and determine whether to shut off unnecessary ports and protocols. Monitor common ports and protocols for command and control activity.
- Enhance monitoring of network and email traffic. Review network signatures and indicators for focused operations activities, monitor for new phishing themes and adjust email rules accordingly, and follow best practices of restricting attachments via email or other mechanisms.
- Patch externally facing equipment. Focus on patching critical and high vulnerabilities that allow for remote code execution or denial of service on externally facing equipment.
- Log and limit usage of PowerShell. Limit the usage of PowerShell to only users and accounts that need it, enable code signing of PowerShell scripts, and enable logging of all PowerShell commands.
- Ensure backups are up to date and stored in an easily retrievable location that is air-gapped from the organizational network.
Patterns of Publicly Known Iranian Advanced Persistent Threats
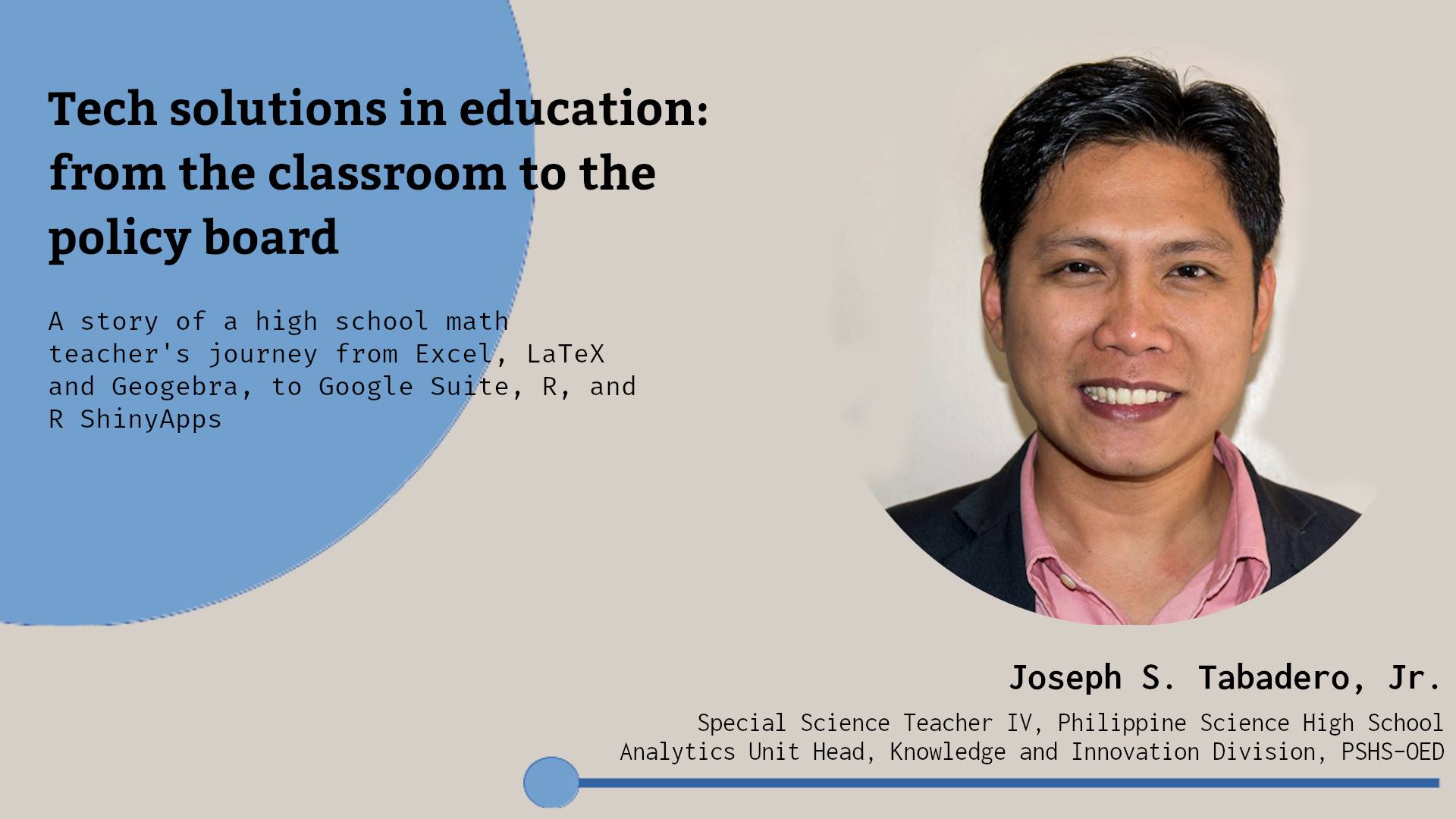
BNS livestreams the Tech Solutions in Education conducted on Dec. 26, 2019
BNS livestreams the Tech Solutions in Education conducted on Dec. 26, 2019
Tech solutions in Education: From the classroom to the policy board
Speaker: Joseph S. Tabadero, Jr.
Part 1 https://www.facebook.com/MBTechNews/videos/372543856944149/
Part 2 https://www.facebook.com/MBTechNews/videos/592489901564432/
Part 3 https://www.facebook.com/MBTechNews/videos/454463468555131/
Part 4 https://www.facebook.com/MBTechNews/videos/416111995789891/
Part 5 https://www.facebook.com/MBTechNews/videos/2531601520451375/
Applied Data Science using R/shinyApp in Education
Mr. Joseph Tabadero will be in Dagupan on Dec 26th (Thursday).
He will conduct a special session on using ShinyApp.
Limited to 15 seats only.
Venue: Module 2 Bonuan Office. We will be live streaming this over Manila Bulletin’s TechNews online
Event Page is now up: https://www.facebook.com/events/2443350725919752/
BNS President to Talk about BASS in PhNOG 2019 Cebu
BNS President to Talk about BASS in PhNOG 2019 Cebu
FOr more details about PhNOg 2019 Cebu click Here
BNS as Speaker in Internet Governance Symposium
[huge_it_slider id=”19 “]
Internet Governance Symposium conducted in Bulacan on December 11, 2018
Wilson Chua as speaker in Cyber Security and Data Privacy Awareness for Every Juan
[huge_it_slider id=”23 “]
Wilson Chua of BNS as speaker in Cyber Security and Data Privacy Awareness for Every Juan as 3RD JISSA University of Luzon Seminar.